Veil-Framework is a cool set of tools available on Kali Linux (and can be downloaded from GitHub on many versions of Linux). Veil allows you to create payload executables that can bypass most antivirus vendors and can be delivered to Windows machines. I have been testing this for the last couple of days now and it works pretty well. I used virustotal.com to test the executable and only a few AV providers detected it. It is a very easy to use command line tool and I had no problems with functionality. It seems to be used in conjunction with metasploit so it may be necessary to install metasploit (if your not using Kali Linux).
I have yet to really try the delivery mechanism (Veil-Catapult) so I am not sure of how good the functionality of this is but I am pretty confident it will work fine (based on the other features I have tried).
I am including a copy of the .EXE file named “undetectable” on my FTP server. If you would like to download and test the file yourself it will be located in:
ftp.chasingtech.net – Folder: Veil-EXE
Login: guest@chasingtech.net Pass: guest1
Here’s the Veil-Framework Website for more information:
Here are the results from my AV (Kaspersky, keep in mind I was able to run the .EXE first and then AV noticed it):
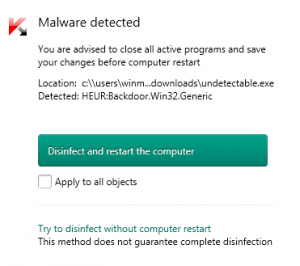
When scanning it on VirusTotal only four AV’s detected it: Anity-AVL, CMC, Qihoo-360, and TheHacker.