I want to preface this article by saying I am by no means an expert. There is plenty of information below that I am still researching and that I do not fully understand. If I mention anything that is incorrect I apologize in advance. I would be glad from anyone with a better understanding or advice on changes.
I have had a Pi-hole running on a raspberry pi 2 for a while now, probably three to four years. Recently, I installed it on a Ubuntu Server I also have running on my network. I never really messed with the settings on the Pi-hole as it was somewhat doing its job and I also have ad-blocking running on most of my machines. A couple of weeks ago, when I installed Pi-hole on my Ubuntu box, I decided it was time to do a deep dive into all of the cool things that Pi-hole can do.
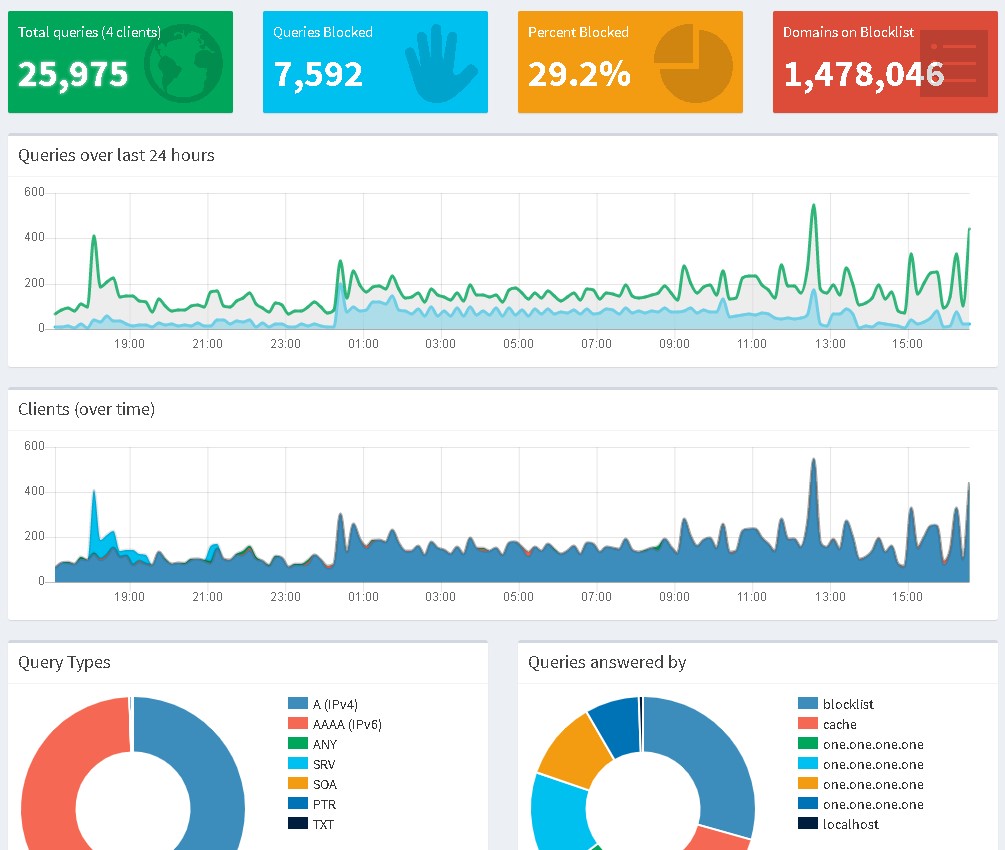
I basically setup both Pi-holes as mirrors of each other and set them on all of my machines as primary and secondary DNS servers. I started looking more into block lists because up to this point I had only been using the default lists on Pi-hole. I decided I wanted to block more and also block malicious websites. At this point, I am blocking more than 1.4 million domains.
I also wanted to try to setup DNS-over-HTTPS. I don’t think I have this working correctly yet and I have also been looking into DNS-over-TLS which I have yet to attempt. I did setup DNS-over-HTTPS both in Google Chrome and Firefox.
For a little background I have included the definitions of DoH and DoT below according to WikiPedia ( https://en.wikipedia.org/wiki/DNS_over_HTTPS & https://en.wikipedia.org/wiki/DNS_over_TLS):
“DNS over HTTPS (DoH) is a protocol for performing remote Domain Name System (DNS) resolution via the HTTPS protocol. A goal of the method is to increase user privacy and security by preventing eavesdropping and manipulation of DNS data by man-in-the-middle attacks[1] by using the HTTPS protocol to encrypt the data between the DoH client and the DoH-based DNS resolver. Encryption by itself does not protect privacy, encryption is simply a method to obfuscate the data. As of March 2018, Google and the Mozilla Foundation started testing versions of DNS over HTTPS.”
“DNS over TLS (DoT) is a security protocol for encrypting and wrapping Domain Name System (DNS) queries and answers via the Transport Layer Security (TLS) protocol. The goal of the method is to increase user privacy and security by preventing eavesdropping and manipulation of DNS data via man-in-the-middle attacks.”
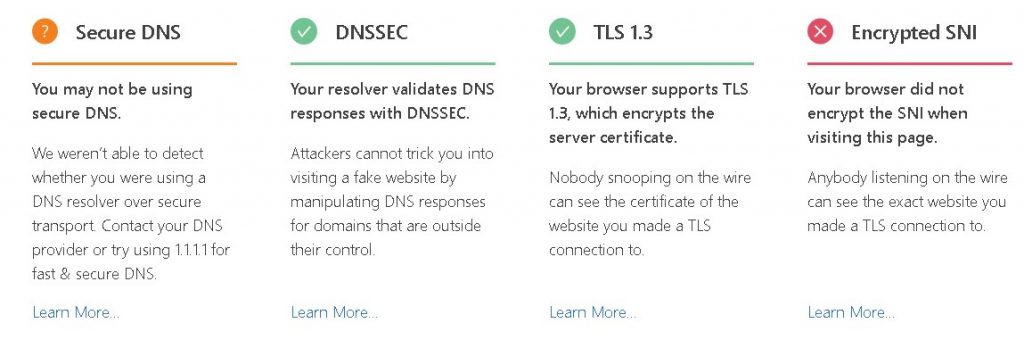
In general using these methods hardens the Pi-hole (or DNS server) and protects the clients of that server from eavesdropping (mostly via man-in-the-middle attacks). Below is a screenshot of the results I get when I use https://www.cloudflare.com/ssl/encrypted-sni/ to check for overall browser security.
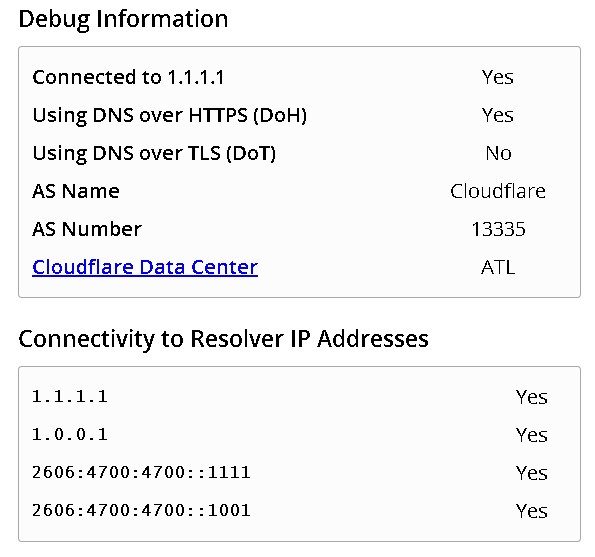
Additionally you can check using 1.1.1.1/help. Below is a screenshot of my results on this page.
Here is the guide I attempted to use to setup DNS-over-HTTPS on Pi-hole: https://docs.pi-hole.net/guides/dns-over-https/ .
Here are the articles I used to setup DNS-over-HTTPS on Chrome and Firefox: https://www.zdnet.com/article/how-to-enable-dns-over-https-doh-in-firefox/ and https://judge.sh/how-to-enable-dns-over-https-on-chrome-right-now/.
My next step will be to work on DNS-over-TLS but I am still not exactly sure how that works. I found this post on Reddit speaking requesting guide: https://www.reddit.com/r/pihole/comments/b1l2sp/dns_over_tls_setup/ which led me here: https://blog.sandchaschte.ch/en/pi-hole-with-dns-over-tls. I can’t yet verify if this works but I will try using this guide to set it up and see if I can get this working. If I can I will add to this article and screenshot my results.
As I said above, I finally started adding some block lists to my server. My main resource was this page: https://discourse.pi-hole.net/t/how-do-i-add-additional-block-lists-to-pi-hole/259. Some of the comments offered additional resources that really helped as well. Especially https://www.malwarepatrol.net/ which is mentioned in a comment by ovizii. You can sign up for a free account and use the block list they provide. I really have only added this one and https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts. So far , just adding these two lists seems to block a lot more content than what was blocked previously. However, if anyone out there has any suggestions on some good lists to use please feel free to add them to the comments section. I would love to try them out.
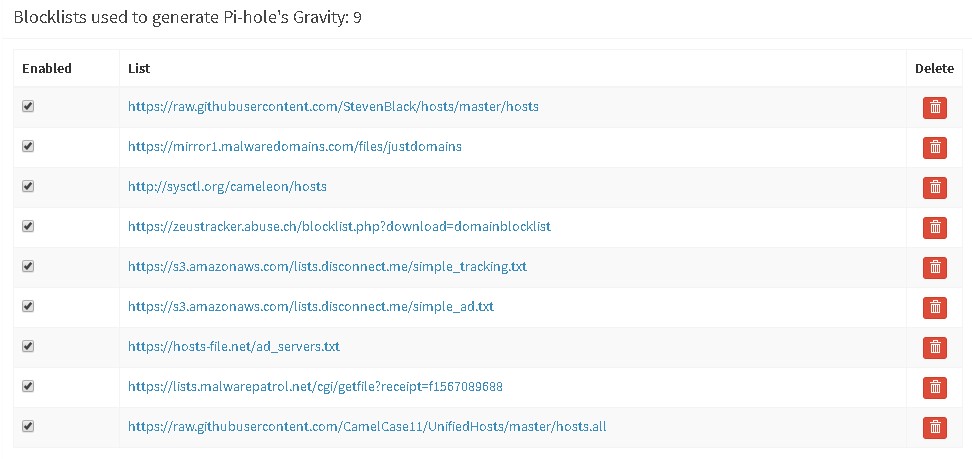
Finally, I wanted to mention that I did start running into some minor issues after adding these block lists. Really only with Microsoft Office. I use Office365 and it appears that the Pi-hole was blocking domains that are required for authentication. It looks like MS Office and OneDrive require an almost constant connection to validate that you actually own the software. I was getting a banner on the top of MS applications saying that they were not valid and upload was blocked. I ended going through the query logs and finding many blocked domains that were pointing to Microsoft and I had to whitelist them to get these applications running again. Unfortunately, it is difficult to know exactly which of these domains are required and if some only appeared to be used for authentication. I couldn’t find any solid information other than this page: https://discourse.pi-hole.net/t/commonly-whitelisted-domains/212. This was useful but didn’t resolve my issue. I had to manually find MS domains and whitelist them in the query log.
Here is an example of my whitelist after adding some of the items from the page above and adding my own items for Office365:
- 106c06cd218b007d-b1e8a1331f68446599e96a4b46a050f5.ams.plex.services
- activation.sls.microsoft.com
- aka.ms
- android.clients.google.com
- api.facebook.com
- app.plex.tv
- apps.skype.com
- apresolve.spotify.com
- attestation.xboxlive.com
- b-api.facebook.com
- b-graph.facebook.com
- bigzipfiles.facebook.com
- c.amazon-adsystem.com
- c.s-microsoft.com
- captive.apple.com
- cdn-gl.imrworldwide.com
- cdn.fbsbx.com
- cert.mgt.xboxlive.com
- client-s.gateway.messenger.live.com
- client.wns.windows.com
- clientconfig.passport.net
- clients3.google.com
- connect.facebook.com
- connectivitycheck.android.com
- connectivitycheck.gstatic.com
- countess.twitch.tv
- cpms.spop10.ams.plex.bz
- cpms35.spop10.ams.plex.bz
- creative.ak.fbcdn.net
- crl.microsoft.com
- ctldl.windowsupdate.com
- dashboard.plex.tv
- def-vef.xboxlive.com
- device.auth.xboxlive.com
- displaycatalog.mp.microsoft.com
- dl.delivery.mp.microsoft.com
- edge-mqtt.facebook.com
- eds.xboxlive.com
- external-lhr0-1.xx.fbcdn.net
- external-lhr1-1.xx.fbcdn.net
- external-lhr10-1.xx.fbcdn.net
- external-lhr2-1.xx.fbcdn.net
- external-lhr3-1.xx.fbcdn.net
- external-lhr4-1.xx.fbcdn.net
- external-lhr5-1.xx.fbcdn.net
- external-lhr6-1.xx.fbcdn.net
- external-lhr7-1.xx.fbcdn.net
- external-lhr8-1.xx.fbcdn.net
- external-lhr9-1.xx.fbcdn.net
- fb.me
- fbcdn-creative-a.akamaihd.net
- g.live.com
- geo-prod.do.dsp.mp.microsoft.com
- gfwsl.geforce.com
- graph.facebook.com
- gravatar.com
- gsp1.apple.com
- help.ui.xboxlive.com
- i.s-microsoft.com
- ipv6.msftncsi.com
- licensing.xboxlive.com
- login.live.com
- login.microsoftonline.com
- m.hotmail.com
- meta-db-worker02.pop.ric.plex.bz
- meta.plex.bz
- meta.plex.tv
- metrics.plex.tv
- mobile.pipe.aria.microsoft.com
- mqtt.c10r.facebook.com
- mscrl.microsoft.com
- msftncsi.com
- nexusrules.officeapps.live.com
- nine.plugins.plexapp.com
- node.plexapp.com
- notify.xboxlive.com
- o1.email.plex.tv
- o2.sg0.plex.tv
- ocsp.msocsp.com
- officeclient.microsoft.com
- onedrive.com
- onedrive.live.com
- outlook.office365.com
- pihole
- plex.tv
- portal.fb.com
- pricelist.skype.com
- products.office.com
- proxy.plex.bz
- proxy.plex.tv
- proxy02.pop.ord.plex.bz
- pubsub-edge.twitch.tv
- pubsub.plex.bz
- pubsub.plex.tv
- s.amazon-adsystem.com
- s.gateway.messenger.live.com
- sa.symcb.com
- scontent-lhr3-1.xx.fbcdn.net
- scontent.fgdl5-1.fna.fbcdn.net
- scontent.xx.fbcdn.net
- settings-win.data.microsoft.com
- spclient.wg.spotify.com
- staging.plex.tv
- star-mini.c10r.facebook.com
- star.c10r.facebook.com
- status.plex.tv
- storeedgefd.dsx.mp.microsoft.com
- support.microsoft.com
- themoviedb.com
- thetvdb.com
- title.auth.xboxlive.com
- title.mgt.xboxlive.com
- tracking.epicgames.com
- tsfe.trafficshaping.dsp.mp.microsoft.com
- tvdb2.plex.tv
- tvthemes.plexapp.com
- tvthemes.plexapp.com.cdn.cloudflare.net
- ui.skype.com
- upload.facebook.com
- v10.events.data.microsoft.com
- v10.vortex-win.data.microsoft.com
- v20.events.data.microsoft.com
- v20.vortex-win.data.microsoft.com
- wdcpalt.microsoft.com
- web.vortex.data.microsoft.com
- www.apple.com
- www.appleiphonecell.com
- www.msftncsi.com
- www.plex.tv
- www.xboxlive.com
- xbox.ipv6.microsoft.com
- xboxexperiencesprod.experimentation.xboxlive.com
- xflight.xboxlive.com
- xkms.xboxlive.com
- xsts.auth.xboxlive.com
Thanks for taking the time to look at my article. I hope my experience can help some of you out there and hope that you guys will correct me, if needed, or help me understand this a bit further. Any useful critiques or items I didn’t think of are greatly appreciated! I will try to update this as I learn more but I do both work full-time and go to college part time so it is hard for me to find the time to add to this blog.
Edit 9/28/19: I wanted to add a couple of items I forgot to originally add or that have been pointed out to me on Reddit. First off, did you guys know you can theme the Pi-hole dashboard. It is extremely simple to do. There are several projects out there to do this.
Here’s one I personally use and like: https://github.com/lkd70/PiHole-Dark.
I also was pointed to this Reddit post by another user who sent me a DM. It contains some huge block lists. I will try them today and see how I like them. Link: https://www.reddit.com/r/pihole/comments/bppug1/introducing_the/
Edit 6/13/20: Today I went ahead and tried reinstalling/updating Cloudflared using this tutorial: https://www.cloudflare.com/ssl/encrypted-sni/. I actually got a much better result than the first time I tried and was able to verify using Cloudflare’s browser check. This tutorial was an easy and quick way to get this work (note: I used the manual method).
As far as I understand the usage of DoH in your browser, you will basically skip your pihole since they connect directly to the DNS server that supports the DoH. Therefore skipping your blocklists. I don’t really see an advantage of setting up DoH within your lan from your browser to your pihole. The only part that makes sense is to have pihole’s requests using DoH outbound.
Huh I never really thought about it like that. It’s still blocking things like Windows telemetry and ads on Android but I guess you are right about DoH on my desktop. Thanks for that! Shows I’m still learning about all this
Sorry for the second reply but any chance you would know to make DoH work on outbound only. I’ll do some research myself but figured I would ask as well. If you have a working guide I’ll link in the article and credit you for it.
Hey that super list suggested by the Reddit user is awesome — I had a moderate block list of 900k (no whitelist necessary and maybe 10 items in my manual blacklist).
The list there raised my block list to 1.7m (though most likely a lot of repeats) but what I loved was most of my black list was already on that new block list. I commented to thank the Reddit user who posted it and got a quick response back. That list is updated daily he says, whitelisting what people need.
Anyway, I’m happy with the addition to my arsenal, and it’s all because of your article that my Google feed fed me. So thanks. (:
Absolutely seems to be a great list! No problem on the article. I just wanted to put up some resources for people and have a place to store what I have been working on. Thanks for the comment!